
Placement Guarantee Program in Cyber Security
For freshers and young professionals
Learn and placed for FREE! Limited Seats.
Get 100% fee refund on course completion!
₹25,000
₹5,000



About the Course
Guaranteed placement intensive cyber security program with hands-on training program designed to equip participants with industry-ready cybersecurity skills. This 90-hour weekday curriculum focuses on practical learning, covering essential cybersecurity concepts, tools, and techniques.
To reinforce learning, participants will also complete 180 hours of practical assignments, ensuring hands-on experience with cybersecurity tools, real-world problem-solving, and practical implementation of security concepts. These assignments provide practical exposure to threat detection, incident response, network security helping participants build a strong foundation in cybersecurity.
Additionally, the program includes weekend sessions (20 hours total) featuring guest lectures from industry experts. These sessions offer valuable insights into cybersecurity trends, career guidance, and advanced security topics, preparing participants for real-world challenges and industry expectations.
Course Contents
- Computer Networks: OSI Model, TCP/IP, TCP 3-Way Handshake
- Protocols & Ports: HTTP, HTTPS, FTP, SMB, RDP, Ports & Vulnerabilities
- Core Cybersecurity Concepts: CIA Triad, Cyber Kill Chain, Importance of Cybersecurity
- Basic Terminologies: Malware & Types, Risk, Threat, Vulnerability, Firewall, IDS/IPS, Phishing, Firewall Setup, VPN, Access Control & Authentication
- Attacks & Monitoring: DoS/DDoS, Man-in-the-Middle (MITM), ARP Poisoning
- Network Reconnaissance: Ping, Traceroute, Whois, Google Dorking, Shodan, Wappalyzer, VirusTotal
- SOC Overview: Role of Security Operations Centers (SOC), Hub-and-Spoke Model
- Threat Intelligence: IOC, IOA, OSINT, GHDB
- Network Security Tools: Wireshark, Zeek
- Detection Mechanisms: IDS vs. IPS, Signature-Based & Anomaly-Based Detection, Firewall Logs Analysis
- MITRE ATT&CK Framework & Cyber Kill Chain
- Threat Mapping: Real-world Threats using ATT&CK Navigator
- Phishing & Email Security: Prevention, Detection, and Incident Analysis
- SIEM Basics: Overview of Splunk & ELK, Event IDs, PowerShell Logs
- Vulnerability Management: Nmap, Open Ports, Vulnerability Scanning Exercise
- Incident Response: Lifecycle, Handling Real DFIR
- Process & Malware Analysis: Process Hacker, Procmon, Process Tree, Analyzing Procmon Logs
- OWASP Top 10: SQL Injection Attack Simulation
- Windows Internals: EXE, DLL, Process, Thread, Process Injection, DLL Injection, Process Hollowing
- PowerShell Security: Decoding & Obfuscation Techniques
- Research & Presentation: Log4j, ProxyShell, EternalBlue, ZeroLogon
- Threat Hunting & Advanced Analysis:
- File-Based Malware Attacks
- Lolbins & Command Line Exploitation
- Lateral Movement & Privilege Escalation
- Forensics:
- Browser History Forensics
- Memory Forensics
- Disk Forensics
- Incident Response Simulation
- Access Control & Zero Trust Security: MFA, Access Control Policies, Zero Trust Model
- APT & TTP Groups: Understanding Advanced Persistent Threats & Tactics
- SOC Perspective on Ransomware Attacks
- Career Guidance & Mock Interviews:
- Interview Questions & Discussions
- Resume Building & LinkedIn Optimization
Course Overview
Lectures
45
Assignment
90
Duration
2 Months
Students
30
Mode
Online
Starts
April 7’2025
Who should join the programme
Students:
- Open to anyone eager to learn and grow in cybersecurity, regardless of educational background.
- A degree in Computer Science, IT, or related fields provides an advantage.
- Fundamental knowledge of networking, programming, and cybersecurity threats helps bridge the gap
Various Technologies and Tools to Learn







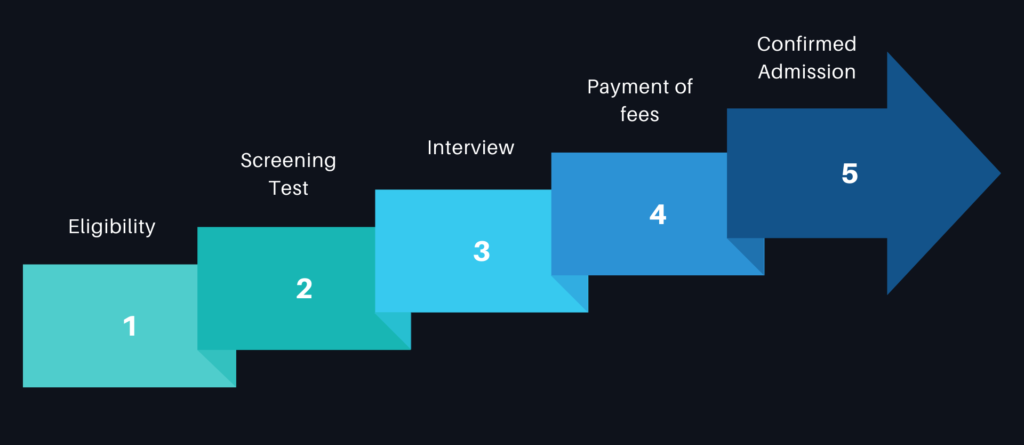
Admission Process
In-demand Cyber skills that you will master.
Cybersecurity Fundamentals
Security & Risk Management
Security Operations & Incidence Management
Threat Hunting & Penetration Testing
Capstone Project & Certificate Evaluation
Soft Skills
Hiring Support
Cyber Apprenticeship
Meet your Instructors
Meet Our Team of Experienced Cyber Security Professionals and Instructors Dedicated to Your Success!
Rohit Mukherjee
B.N.M Institute of Technology, Bangalore (Electrical & Electronics Engineering)
Certifications: Cyber Threat Hunting Level 1 – Active Countermeasures, Become an Incident Handler – Cybrary, Malware Analysis – Pluralsight, Offensive Penetration Testing – Cybrary, AWS Certified Cloud Practitioner – Cybrary, NSE 1 & NSE 2 [Network Security Associate] – Fortinet, Certified Network Security Specialist – ICSI
Cyber security professional with extensive experience in Incident Response, Threat Hunting, and Malware Analysis. Specializes in creating attack chains, identifying new malware campaigns, and performing advanced cyber defense techniques. Expertise in handling critical incidents, business email compromise, and phishing assessments.
Everything you need for providing world-class support.
Guaranteed Placement Program
<details about guaranteed placement to come here and in pointers>
- Hiring support and career guidance
- 2 weeks dedicated training in development of soft skills
- Guided preparation for interview including resume preparation



Career Support

Career Support
Get help from our dedicated careers team through 1-on-1 guidance to land your dream job

Professional Coaching
1-to-1 session with our professional coach to develop soft skills, communication and interview preparation

Employer partners
Get employed immediately through our partner companies and cyber security employers
Companies hiring Cybersecurity Professionals
















Ready to kickstart your career in Cybersecurity?
Free Course | Assured Placement | Only 30 Seats | Admission via Test & Interview
Trusted by hundreds of customers.

Naveen Reddy
Having seen the quality of the course content, I am sure that the learners will gain great deal of advantage in cracking interviews for Cybersecurity careers.

Ankita Sharma
The practical aspect of the training curriculum being provided as part of T-CCBP course will prepare students for facing the real world challenges with confidence.

Vineet R Bhatt
Apart from providing cyber defence and hacking skills, the course will equip learners with most essential soft skills that will help learners crack interviews with ease

Jasbir Solanki
The certifications and courses being provided by team Hacker Central will be of very high value to learners seeking to kickstart their careers in Cybersecurity
FAQ
Common Questions About Us
Frequently Asked Questions.
This program is a Guaranteed placement intensive cyber security program designed to provide participants with practical knowledge and hands-on experience in cybersecurity. The curriculum includes essential cybersecurity topics such as network security, threat intelligence, vulnerability management, and digital forensics to prepare participants for careers in cybersecurity.
The duration of the program is 45 days. During this period, participants will undergo structured training consisting of live interactive sessions and practical laboratory exercises.
The program consists of 90 hours of live classes and 180 hours of practical lab sessions. This structured approach ensures that participants acquire both theoretical knowledge and practical skills required for cybersecurity roles.
The course is delivered online and follows a work-integrated learning approach. This allows participants to participate remotely while gaining hands-on experience with cybersecurity tools and real-world scenarios.
The next batch of the program begins on April 7, 2025. Since the program follows a cohort-based structure, it is advisable to register in advance to secure a spot.
While the course is open to participants and professionals from various backgrounds, a prerequisites test is scheduled on March 22, 2025 to assess foundational knowledge. This test will help determine the applicant’s readiness for the program.
